Binary options strategy mmx
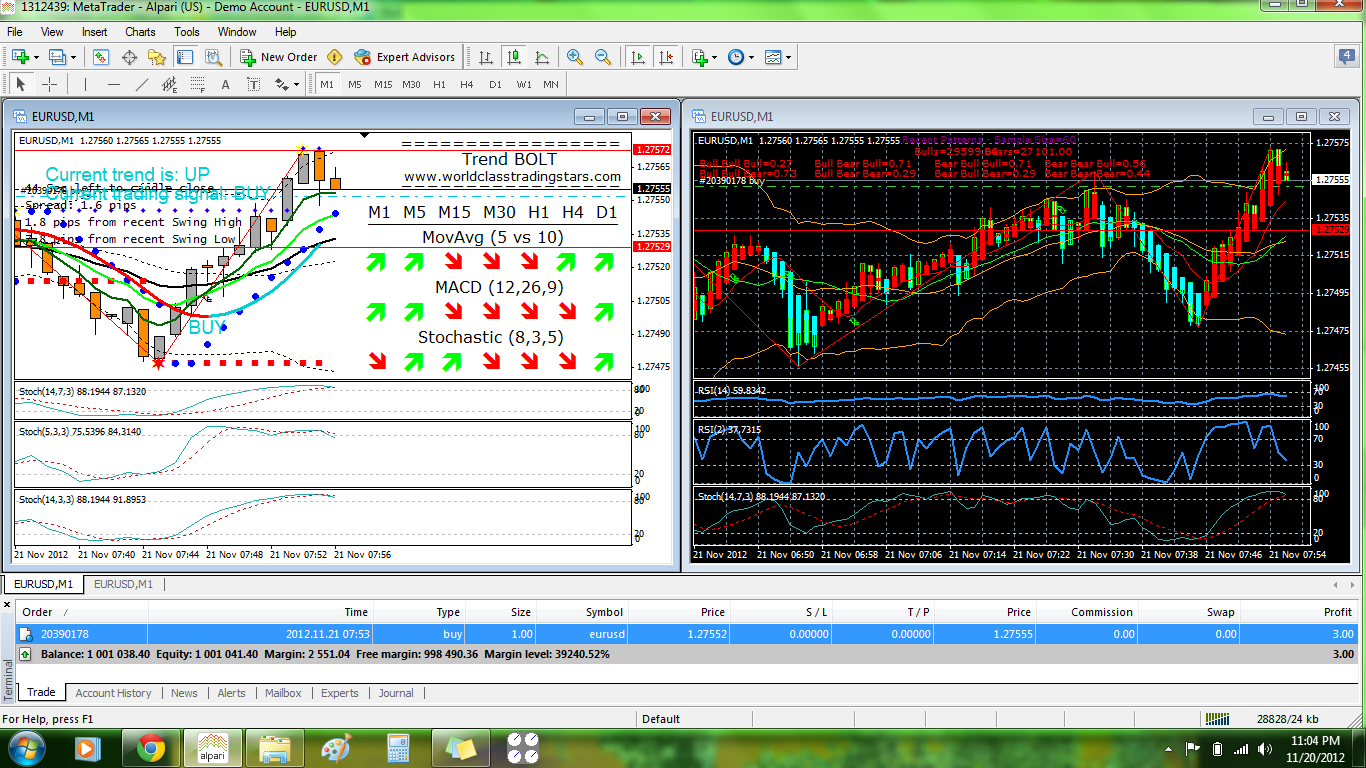
This document is a reference manual for the LLVM assembly language. It is the common code representation used throughout all phases of the LLVM compilation strategy. The LLVM code representation is designed to be used in three different forms: as an in-memory compiler IR, as an on-disk bitcode representation suitable for fast loading by a Just-In-Time compilerand as a human readable assembly language representation. This allows LLVM to provide a powerful intermediate representation for efficient compiler transformations and analysis, while providing a natural means to debug and visualize the transformations. The three different forms of LLVM are all equivalent. This document describes binary human readable representation and notation. The LLVM representation aims to be light-weight and low-level mmx being expressive, typed, and extensible at the same time. By providing type information, LLVM can be used as the target of optimizations: for example, through pointer analysis, it can be proven that a C automatic variable is never accessed outside of the current function, allowing it to be promoted to a simple SSA value instead of a memory location. The LLVM infrastructure provides a verification pass that may be used to verify that an LLVM module is well formed. This pass is automatically run by the parser after parsing input assembly and by the optimizer before it outputs bitcode. The violations pointed out by the verifier pass indicate bugs in transformation passes or input to the parser. LLVM identifiers come in two basic types: global and local. Additionally, unnamed identifiers allow a compiler to quickly come up with a temporary variable without having to avoid symbol table conflicts. Reserved words in LLVM are very similar to reserved words in other languages. When demonstrating instructions, we will follow an instruction with a comment that defines the type and name of value produced. Each module consists of functions, global variables, and symbol table entries. Modules may be combined together with the LLVM linker, which merges function and global variable definitions, resolves forward declarations, and merges symbol table entries. In general, a module is made up of a list of global values where both functions and global variables are global values. Global values are represented by a pointer to a memory location in this case, a pointer to an array of char, and a pointer to a functionand have one of the following linkage types. When two global variables with appending linkage are linked together, the two global arrays are appended together. LLVM functionscalls and invokes can all have an optional calling convention specified for the call. The following calling conventions are supported by LLVM, and more may be added in the future: This calling convention has been implemented specifically for use by the Glasgow Haskell Compiler GHC. It passes everything in registers, going to extremes to achieve this by disabling callee save registers. This calling convention should not be used lightly but only for specific situations such as an alternative to the register pinning performance technique often used when implementing functional programming languages. At the moment only X86 supports this convention and it has the following limitations: This calling convention supports tail call optimization but requires both the caller and callee are using it. This calling convention attempts to make the code in the caller as unintrusive as possible. This alleviates the burden of saving and recovering a large register set before and after the call in the caller. If the arguments are passed in callee-saved registers, then they will be preserved by the callee across the call. The idea behind this convention is to support calls to runtime functions that have a hot path and a cold path. This calling convention will be used by a future version of the ObjectiveC runtime and should therefore still be considered experimental at this time. Although this convention was created to optimize certain runtime calls to the ObjectiveC runtime, it is not limited to this runtime and might be used by other runtimes in the future too. The current implementation only supports Xbut the intention is to support more architectures in the future. This calling convention attempts to make the code in the caller even less intrusive than the PreserveMost calling convention. This removes the burden of saving and recovering a large register set before and after the call in the caller. This calling convention, like the PreserveMost calling convention, will be used by a future version of the ObjectiveC runtime and should be considered experimental at this time. The access function generally has an entry block, an exit block and an initialization block that is run at the first time. The entry and exit blocks can access a few TLS IR variables, each access will be lowered to a platform-specific sequence. This calling convention aims to minimize overhead in the caller by preserving as many registers as possible all the registers that are perserved on the fast path, composed of the entry and exit blocks. A symbol with internal or private linkage must have default visibility. Not all targets support thread-local variables. Optionally, a TLS model may be specified: The models correspond to the ELF TLS models; see ELF Handling For Thread-Local Storage for more information on under which circumstances the different models may be used. The target may choose a different TLS model if the specified model is not supported, or if a better choice of model can be made. A model can also be specified in an alias, but then it only governs how the alias is accessed. It will not have any effect in the aliasee. For platforms without linker support of ELF TLS model, the -femulated-tls flag can be used to generate GCC compatible emulated TLS code. Literal types are uniqued structurally, but identified types are never uniqued. Only literal types are uniqued in recent versions of LLVM. Note: non-integral pointer types are a work in progress, and they should be considered experimental at this time. Non-integral pointer types represent pointers that have an unspecified bitwise representation; that is, the integral representation may be target dependent or unstable not backed by a fixed integer inttoptr instructions converting integers to non-integral pointer types are ill-typed, and so are ptrtoint instructions converting values of non-integral pointer types to integers. Vector versions of said instructions are ill-typed as well. Either global variable definitions or declarations may have an explicit section to be placed in and may have an optional explicit alignment specified. A variable may be defined as a global constantwhich indicates that the contents of the variable will never be modified enabling better optimization, allowing the global data to be placed in the read-only section of an executable, etc. Note that variables that need runtime initialization cannot be marked constant as there is a store to the variable. LLVM explicitly allows declarations of global variables to be marked constant, even if the final definition of the global is not. As SSA values, global variables define pointer values that are in scope i. Constants marked like this can be merged with other constants if they have the same initializer. A global variable may be declared to reside in a target-specific numbered address strategy. The default address space is zero. The address space qualifier must precede any other attributes. LLVM allows an explicit section to be specified for globals. If the target supports it, it will emit globals to the section specified. Additionally, the global can placed in a comdat if the target has the necessary support. Mmx default, global initializers are optimized by assuming that global variables defined within the module are not modified from their initial values before the start of the global initializer. An explicit alignment may be specified for a global, which must be a power of 2. If not present, or if the alignment is set to zero, the alignment of the global is set by the target to whatever it feels convenient. If an explicit alignment is specified, the global is forced to have exactly that alignment. Targets and optimizers are not allowed to over-align the global if the global has an assigned section. In this case, the extra mmx could be observable: for example, code could assume that the globals are densely packed in their section and try to iterate over them as an array, alignment padding would break this iteration. A function definition contains a list of basic blocks, forming the CFG Control Flow Graph for the function. Each basic block may optionally start with a label giving the basic block a symbol table entrycontains a list of instructions, and ends with a terminator instruction such as a branch or function return. The first basic block in a function is special in two ways: it is immediately executed on entrance to the function, and it is not allowed to have predecessor basic blocks i. Because the block can have no predecessors, it also cannot have any PHI nodes. LLVM allows an explicit section to strategy specified for functions. If the target supports it, it will emit functions to the section specified. Additionally, the function can be placed in a COMDAT. An explicit alignment may be specified for a function. If not present, or if the alignment is set to zero, the alignment of the function is set by the target to whatever it feels convenient. If an explicit alignment is specified, the function is forced to have at least that much alignment. All alignments must be a power of 2. They are just a new symbol and metadata for an existing position. Note that some system linkers might not correctly handle dropping a weak symbol that is aliased. They are just a new symbol that dynamic linker resolves at runtime by calling a options function. IFuncs have a name and a resolver that is a function called by dynamic linker that returns address of another function associated with the name. Comdats have a name which represents the COMDAT key. All global objects that specify this key will only end up in the final object file if the linker chooses that key over some other key. Aliases are placed in the same COMDAT that their aliasee computes to, if any. Comdats have a selection kind to provide input on how the linker should choose between keys in two different object files. There are some restrictions on the properties of the global object. It, or an alias to it, must have the same name as the COMDAT group when targeting COFF. The contents and size of this object may be used during link-time to determine which COMDAT groups get selected depending on the selection kind. Because the name of the object must match the name of the COMDAT group, the linkage of the global object must not be local; local symbols can get renamed if a collision occurs in the symbol table. This is necessary because both globals belong to different COMDAT groups and COMDATs, at the object file level, are represented by sections. Note that certain IR constructs like global variables and functions may create COMDATs in the object file in addition to any which are specified using COMDAT IR. This arises when the code generator is configured to emit globals in individual sections e. Named metadata is a collection of metadata. Metadata nodes but not metadata strings are the only valid operands for a named metadata. Parameter attributes are used to communicate additional information about the result or parameters of a function. Parameter attributes are considered to be part of the function, not of the function type, so functions with different parameter attributes can have the same function type. Parameter attributes are simple keywords that follow the type specified. If multiple parameter attributes are needed, they are space separated. This indicates that the pointer parameter should really be passed by value to the function. The attribute implies that a hidden copy of the pointee is made between the caller and the callee, so the callee is unable to modify the value in the caller. This attribute is only valid on LLVM pointer arguments. It is generally used to pass structs and arrays by value, but is also valid on pointers to scalars. The copy is considered to belong to the caller not the callee for example, readonly functions should not write to byval parameters. This is not a valid attribute for return values. The byval attribute also supports specifying an alignment with the align attribute. It indicates the alignment of the stack slot to form and the known alignment of the pointer specified to the call site. If the alignment is not specified, then the code generator makes a target-specific assumption. The inalloca argument attribute allows the caller to take the address of outgoing stack arguments. An inalloca argument must be a pointer to stack memory produced by an alloca instruction. The alloca, or argument allocation, must also be tagged with the inalloca keyword. Only the last argument may have the inalloca attribute, and that argument is guaranteed to be passed in memory. An argument allocation may be used by a call at most once because the call may deallocate it. The inalloca attribute cannot be used in conjunction with other attributes that affect argument storage, like inregnestsretor byval. When the call site is reached, the argument allocation must have been the most recent stack allocation that is still live, or the results are undefined. See Design and Usage of the InAlloca Attribute for more information on how to use this attribute. This indicates that the pointer value may be assumed by the optimizer to have the specified alignment. Note that this attribute has additional semantics when combined with the byval attribute. This indicates that objects accessed via pointer values based on the argument or return value are not also accessed, during the execution of the function, via pointer values not based on the argument or return value. The attribute on a return value also has additional semantics described below. The caller shares the responsibility with the callee for ensuring that these requirements are met. For further details, please see the discussion of the NoAlias response in alias analysis. Note that this definition of noalias is intentionally similar to the definition of restrict in C99 for function arguments. Furthermore, the semantics of the noalias attribute on return values are stronger than the semantics of the attribute when used on function arguments. On function return values, the noalias attribute indicates that the function acts like a system memory allocation function, returning a pointer to allocated options disjoint from the storage for any other object accessible to the caller. This attribute is motivated to model and optimize Swift error handling. It can be applied to a parameter with pointer to pointer type or a pointer-sized alloca. At the call site, the actual argument that corresponds to a swifterror parameter has to come from a swifterror alloca or the swifterror parameter of the caller. A swifterror value either the parameter or the alloca can only be loaded and stored from, or used as a swifterror argument. This is not a valid attribute for return values and can only be applied to one parameter. These constraints strategy the calling convention to optimize access to swifterror variables by associating them with a specific register at call boundaries rather than placing them in memory. Since this does change the calling convention, a function which uses the swifterror attribute on a parameter is not ABI-compatible with one which does not. Specifying a GC strategy will cause the compiler to alter its output in order to support the named garbage collection algorithm. Note that LLVM itself does not contain a garbage collector, this functionality is restricted to generating machine code which can interoperate with a collector provided externally. The purpose of this feature is to allow frontends to associate language-specific binary metadata with specific functions and make it available through the function pointer while still allowing the function pointer to be called. The function will be placed such that the beginning of the prefix data is aligned. A function may have prefix data but no body. The prologue attribute allows arbitrary code encoded as bytes to be inserted prior to the function body. This can be used for enabling function hot-patching and instrumentation. To maintain the semantics of ordinary function calls, the prologue data must have a particular format. This allows the inliner and other passes to reason about the semantics of the function definition without needing to reason about the prologue data. Obviously this makes the format of the prologue data highly target dependent. The personality attribute permits functions to specify what function to use for exception handling. Attribute groups are groups of attributes that are referenced by objects within the IR. They are important for keeping. In the degenerative case of a. An attribute group is a module-level object. An object may refer to more than one attribute group. In that situation, the attributes from the different groups are merged. Function attributes are considered to be part of the function, not of the function type, so functions with different function attributes can have the same function type. Function attributes are simple keywords that follow the type specified. If multiple attributes are needed, they are space separated. The referenced parameters must be integer types. This is only valid at call sites for direct calls to functions that are declared with the nobuiltin attribute cold This attribute indicates that this function is rarely called. When computing edge weights, basic blocks post-dominated by a cold function call are also considered to be cold; and, thus, given low weight convergent In some parallel execution models, there exist operations that cannot be made control-dependent on any additional values. We call such operations convergentand mark them with this attribute. When it appears on a function, it indicates that calls to this function should not be made control-dependent on additional values. This is particularly useful on indirect calls; without this we may treat such calls as though the target is non-convergent. The optimizer may remove the convergent attribute on functions when it can prove that the function does not execute any convergent operations. This attribute indicates that calls to the function cannot be duplicated. A call to a noduplicate function may be moved within its parent function, but may not be duplicated within its parent function. A function containing a noduplicate call may still be an inlining candidate, provided that the call is not duplicated by inlining. That implies that the function has internal linkage and only has one call site, so the original call is dead after inlining. Strategy function attribute indicates that most optimization passes will skip this function, with the exception of interprocedural optimization passes. This attribute cannot be used together with the alwaysinline attribute; this attribute is also incompatible with the minsize attribute and the optsize attribute. This attribute requires the noinline attribute to be specified on the function as well, so the function is never inlined into any caller. Only functions with the alwaysinline attribute are valid candidates for inlining into the body of this function. This attribute tells the code generator that the code generated for this function needs to follow certain conventions that make it possible for a runtime function to patch over it later. The exact effect of this attribute depends on its string value, for which there currently is one legal possibility: "prologue-short-redirect" This style of patchable function is intended to support patching a function prologue to redirect control away from the function in a thread safe manner. It guarantees that the first instruction of the function will be large enough to accommodate a short jump instruction, and will be sufficiently aligned to allow being fully changed via an atomic compare-and-swap instruction. While the first requirement can be satisfied by inserting large enough NOP, LLVM can and will try to re-purpose an existing instruction i. All of the semantic effects the patching may have to be separately conveyed via the linkage type. On a function, this attribute indicates that the function computes its result or decides to unwind an exception based strictly on its arguments, without dereferencing any pointer arguments or otherwise accessing binary mutable state e. It does not write through any pointer arguments including byval arguments and never changes any state visible to callers. This means that it cannot unwind exceptions by calling the C exception throwing methods. On an argument, this attribute indicates that the function does not dereference that pointer argument, even though it may read or write the memory that the pointer points to if accessed through other pointers. On a function, this attribute indicates that the function does not write through any pointer arguments including byval arguments or otherwise modify any state e. It may dereference pointer arguments and read state that may be set in the caller. A readonly function always returns the same value or unwinds an exception identically when called with the same set of arguments and global state. It cannot unwind an exception by calling the C exception throwing methods. On an argument, this attribute indicates that the function does not write through this pointer argument, even though it may write to the memory that the pointer points to. On a function, this attribute indicates that the function may write to but does not read from memory. On an argument, this attribute indicates that the function may write to but does not read through this pointer argument even though it may read from the memory that the pointer points to. This attribute indicates that SafeStack protection is enabled for this function. This attribute indicates that the function should emit a stack smashing protector. A heuristic is used to determine if a function needs stack protectors or not. The heuristic used will enable protectors for functions with: Variables that are identified as requiring a protector will be arranged on the stack such that they are adjacent to the stack protector guard. This attribute indicates that the function should always emit a stack smashing protector. This overrides the ssp function attribute. Variables that are identified as requiring a protector will be arranged on the stack such that they are adjacent to the stack protector guard. This attribute causes a strong heuristic to be used when determining if a function needs stack protectors. The strong heuristic will enable protectors for functions with: Variables that are identified as requiring a protector will be arranged on the stack such that they are adjacent to the stack protector guard. The specific layout rules are: This overrides the ssp function attribute. Operand bundles are tagged sets of SSA values that can be associated with certain LLVM instructions currently only call s and invoke s. This reflects the fact that the operand bundles are conceptually a part of the call or invokenot the callee being dispatched to. Operand bundles are a generic mechanism intended to support runtime-introspection-like functionality for managed languages. While the exact semantics of an operand bundle depend options the bundle tag, there are certain limitations to how much the presence of an operand bundle can influence the semantics of a program. As long as the behavior of an operand bundle is describable within these restrictions, LLVM does not need to have special knowledge of the operand bundle to not miscompile programs containing it. Deoptimization operand bundles are characterized by the "deopt" operand bundle tag. There can be at most one "deopt" operand bundle attached to a call site. Exact details of deoptimization is out of scope for the language reference, but it usually involves rewriting a compiled frame into a set of interpreted frames. Deoptimization operand bundles do not capture their operands except during deoptimization, in which case control will not be returned to the compiled frame. The inliner knows how to inline through calls that have deoptimization operand bundles. Funclet operand bundles are characterized by the "funclet" operand bundle tag. These operand bundles indicate that a call site is within a particular funclet. There can be at most one "funclet" operand bundle attached to a call site and it must have exactly one bundle operand. GC transition operand bundles are characterized by the "gc-transition" operand bundle tag. These operand bundles mark a call as a transition between a function with one GC strategy to a function with a different GC strategy. If coordinating the transition between GC strategies requires additional code generation at the call site, these bundles may contain any values that are needed by the generated code. For more details, see GC Transitions. These blocks are internally concatenated by LLVM and treated as a single unit, but may be separated in the. The syntax is very simple module asm "inline asm code goes here" module asm "more can go here" The strings can contain any character by escaping non-printable characters. A module may specify a target specific data layout string that specifies how data is to be laid out in memory. Each specification starts with a letter and may include other information after the letter to define some aspect of the data layout. When constructing the data layout for a given target, LLVM starts with a default set of specifications which are then possibly overridden by the specifications in the datalayout keyword. The default specifications are given in this list: The function of the data layout string may not be what you expect. Notably, this is not a specification from the frontend of what alignment the code generator should use. Instead, if specified, the target data layout is required to match what the ultimate code generator expects. This string is used by the mid-level optimizers to improve code, and this only works if it matches what the ultimate code generator uses. There is no way to generate IR that does not embed this target-specific detail into the IR. A module may specify a target triple string that describes the target host. Any memory access must be done through a pointer value associated with an address range of the memory access, otherwise the behavior is undefined. LLVM IR does not associate types with memory. The result type of a load merely indicates the size and alignment of the memory from which to load, as well as the interpretation of the value. The first operand type of a store similarly only indicates the size and alignment of the store. Consequently, type-based alias analysis, aka TBAA, aka -fstrict-aliasingis not applicable to general unadorned LLVM IR. Metadata may be used to encode additional information which specialized optimization passes may use to implement type-based alias analysis. The optimizers must not change the number of volatile operations or change their order of execution relative to other volatile operations. The optimizers may change the order of volatile operations relative to non-volatile operations. Platforms may rely on volatile loads and stores of natively supported data width to be executed as single instruction. For example, in C this holds for an l-value of volatile primitive type with native hardware support, but not necessarily for aggregate types. The frontend upholds these expectations, which are intentionally unspecified in the IR. The LLVM IR does not define any way to start parallel threads of execution or to register signal handlers. For a more informal introduction to this model, see the LLVM Atomic Instructions and Concurrency Guide. Note that program order does not introduce happens-before edges between a thread and signals executing inside that thread. For the purposes of this section, initialized globals are considered to have a write of the initializer which is atomic and happens before any other read or write of the memory in question. For each byte of a read R, R byte may see any write to the same byte, except: R returns the value composed of the series of bytes it read. This implies that some bytes within the value may be undef without the entire value being undef. Note that in cases where none of the atomic intrinsics are used, this model places only one restriction on IR transformations on top of what is required for single-threaded execution: introducing a store to a byte which might not otherwise be stored is not allowed in general. Specifically, in the case where another thread might write to and read from an address, introducing a store can change a load that may see exactly one write into a load that may see multiple writes. Atomic instructions cmpxchgatomicrmwfenceatomic loadand atomic store take ordering parameters that determine which other atomic instructions on the same address they synchronize with. For a simpler introduction to the ordering constraints, see the LLVM Atomic Instructions and Concurrency Guide. LLVM IR floating-point binary ops faddfsubfmulfdivfremfcmp have the following flags that can be set to enable strategy unsafe floating point operations Use-list directives encode the in-memory order of each use-list, allowing the order to be recreated. Use-list directives may appear at function scope or global scope. They are not instructions, and have no effect on the semantics of the IR. It is then preserved through the IR and bitcode. This is currently necessary to generate a consistent unique global identifier for local functions used in profile data, which prepends the source file name to the local function name. Being typed enables a number of optimizations to be performed on the intermediate representation directly, without having to do extra analyses on the side before the transformation. It consists of a return type and a list of formal parameter types. Optionally, the parameter list may include a typewhich indicates that the function takes a variable number of arguments. Variable argument functions can access their arguments with the variable argument handling intrinsic functions. The first class types are perhaps the most important. Values of these types are the only ones which can be produced by instructions. The integer type is a very simple type that simply specifies an arbitrary bit width for the integer type desired. Any bit width from 1 bit to about 8 million can be specified iN The number of bits the integer will occupy is specified by the N value. The operations allowed on it are quite limited: parameters and return values, load and store, and bitcast. Pointers are commonly used to reference objects in memory. Pointer types may have an optional address space attribute defining the numbered address space where the pointed-to object resides. The default address space mmx number zero. The semantics of non-zero address spaces are target-specific. Vector strategy are used when multiple primitive data are operated in parallel using a single instruction SIMD. A vector type requires a size number of elements and an underlying primitive data type. Arrays and structs are aggregate types. Vectors are not considered to be aggregate types. The array type is a very simple derived type that arranges elements sequentially in memory. There is no restriction on indexing beyond the end of the array implied by a static type though there are restrictions on indexing beyond the bounds of an allocated object in some cases. The structure type is used to represent a collection of data members together in memory. The elements of a structure may be any type that has a size. In non-packed structs, padding between field types is inserted as defined by the DataLayout string in the module, which is required to match what the underlying code generator expects. A literal structure is defined inline with other types e. Literal types are uniqued by their contents and can never be recursive or opaque since there is no way to write one. This section describes them all and their syntax. The one non-intuitive notation for constants is the hexadecimal form of floating point constants. The only time hexadecimal floating point constants are required and the only time that they are generated by the disassembler is when options floating point constant must be emitted but it cannot be represented as a decimal floating point number in a reasonable number of digits. When using the hexadecimal form, constants of types half, float, and double are represented using the 16-digit form shown above which matches the IEEE754 representation for double ; half and float values must, however, be exactly representable as IEEE half and single precision, respectively. Hexadecimal format is always used for long double, and there are three forms of long double. The 80-bit format used by x86 is represented as 0xK followed by 20 hexadecimal digits. The bit format used by PowerPC two adjacent doubles is represented by 0xM followed by 32 hexadecimal digits. The IEEE bit format is represented by 0xL followed by 32 hexadecimal digits. Long doubles will only work if they match the long double format on your target. The IEEE 16-bit format half precision is represented by 0xH followed by 4 hexadecimal digits. All hexadecimal formats are big-endian sign bit at the left. Complex constants are a potentially recursive combination of simple constants and smaller complex constants. The addresses of global variables and functions are always implicitly valid link-time constants. These constants are explicitly referenced when the identifier for the global is used and always have pointer type. Undefined values are useful because they indicate to the compiler that the program is well defined no matter what value is used. This gives the compiler more freedom to optimize. Instead, the value is logically read from arbitrary registers that happen to be around when needed, so the value is not necessarily consistent over time. However, in the second example, we can make a more aggressive assumption: because the undef is allowed to be an arbitrary value, we are allowed to assume that it could be zero. Since a divide by zero has undefined behaviorwe are allowed to assume that the operation does not execute at all. This allows us to delete the divide and all code after it. However, a store to an undefined location could clobber arbitrary memory, therefore, it has undefined behavior. Poison values are similar to undef valueshowever they also represent the fact that an mmx or constant expression that cannot evoke side effects has nevertheless detected a condition that results in undefined behavior. There is currently no way of representing a poison value in the IR; they only exist when produced by operations such as add with the nsw flag. Taking the address of the entry block is illegal. Pointer equality tests between labels addresses results in undefined behavior — though, again, comparison against null is ok, and no label is equal to the null pointer. This may be passed around as an opaque pointer sized value as long as the bits are not inspected. This allows ptrtoint and arithmetic to be performed on these values so long as the original value is reconstituted before the indirectbr instruction. Finally, some targets may provide defined semantics when using the value as the operand to an inline assembly, but that is target specific. Constant expressions are used to allow expressions involving other constants to be used as constants. Constant expressions may be of any first class type and may involve any LLVM operation that does not have side effects e. The following is strategy syntax for constant expressions: LLVM supports inline assembler expressions as opposed to Module-Level Inline Assembly through the use of a special value. This value represents the inline assembler as a template string containing the instructions to emita list of operand constraints stored as a stringa flag that indicates whether or not the inline asm expression has side effects, and a flag indicating whether the function containing the asm needs to align its stack conservatively. The assumed dialect is ATT. Currently, ATT and Intel are the only supported dialects. The constraint list is a comma-separated string, each element containing one or more constraint codes. There are three different types of constraints, which are distinguished by a prefix symbol in front of the constraint code: Output, Input, and Clobber. The constraints must always be given in that order: outputs first, then inputs, then clobbers. They cannot be intermingled. This indicates that the assembly will write to this operand, and the operand will then be made available as a return value of the asm expression. Output constraints do not consume an argument from the call instruction. Except, see below about indirect outputs. Normally, it is expected that no output locations are written to by the assembly expression until all of the inputs have been read. As such, LLVM may assign the same register to an output and an input. If this is not safe e. Input constraints do not have a prefix — just the constraint codes. Each input constraint will consume one argument from the call instruction. It is not permitted for the asm to write to any input register or memory location unless that input is tied to an output. Note also that multiple inputs may all be assigned to the same register, if LLVM can determine that they necessarily all contain the same value. In that case, no other input may share the same register as the input tied to the early-clobber even when the other input has the same value. You may only tie an input to an output which has a register constraint, not a memory constraint. Only a single input may be tied to an output. Firstly, the registers are not guaranteed to be consecutive. So, on those architectures that have instructions which operate on multiple consecutive instructions, this is not an appropriate way to support them. The hardware then loads into both the named register, and the next register. This feature of inline asm would not be useful to support that. A few of the targets provide a template string modifier allowing explicit access to the second register of a two-register operand e. MIPS LMand D On such an architecture, you can actually access the second allocated register yet, still, not any subsequent ones. This indicates that the asm will write to or read from the contents of an address provided as an input argument. Note that in this way, indirect outputs act more like an input than an output: just like an input, they consume an argument of the call expression, rather than producing a return value. This is most typically used for memory constraint, e. It is also possible to use an indirect register constraint, but only on output e. This will cause LLVM to allocate a register for an output value normally, and then, separately emit a store to the address provided as input, after the provided inline asm. I would recommend not using it. A clobber does not consume an input operand, nor generate an output. Clobbers cannot use any of the general constraint code letters — they may use only explicit register constraints, e. A Constraint Code is either a single letter e. A single constraint may include one or more than constraint code in it, leaving it up to LLVM to choose which one to use. This is included mainly for compatibility with the translation of GCC inline asm coming from clang. There are two ways to specify binary, and either or both may be used in an inline asm constraint list: Putting those together, you might have a two operand constraint string like "rm r,ri rm". This indicates that if operand 0 is r or mthen operand 1 may be one of r or i. If operand 0 is rthen operand 1 may be one of r or m. But, operand 0 and 1 cannot both be of type m. However, the use of either of the alternatives features is NOT recommended, as LLVM is not able to make an intelligent choice about which one to use. At the point it currently needs to choose, not enough information is available to do so in a smart way. And, if given multiple registers, or multiple register classes, it will simply choose the first one. The constraint codes are, in general, expected to behave the same way they do in GCC. A mismatch in behavior between LLVM and GCC likely indicates a bug in LLVM. The modifiers are, in general, expected to behave the same way they do in GCC. SystemZ implements only nand does not support any of the other target-independent modifiers. If present, the code generator will use the integer as the location cookie value when report errors through the LLVMContext error reporting mechanisms. This allows a front-end to correlate backend errors that occur with inline asm back to the source code that produced it. For example call void asm sideeffect "something bad""" ,! If options MDNode contains multiple constants, the code generator will use the one that corresponds to the line of the asm that the error occurs on. LLVM IR allows metadata to be attached to instructions in the program that can convey extra information about the code to the optimizers and code generator. One example application of metadata is source-level mmx information. There are two metadata primitives: strings and nodes. Metadata does not have a type, and is not a value. If referenced from a call instruction, it uses the metadata type. A metadata string is a string surrounded by double quotes. Metadata nodes are represented with notation similar to structure constants a comma separated list of elements, surrounded by braces and preceded by an exclamation point. Metadata nodes can have any values as their operand. They can also occur when transformations cause uniquing collisions when metadata operands change. A named metadata is a collection of metadata nodes, which can be looked up in the module symbol table. Metadata can be attached to an instruction. Metadata can also be attached to a function definition. Specialized metadata nodes are custom data structures in metadata as opposed to generic tuples. Their fields are labelled, and can be specified in any order. DICompileUnit nodes represent a compile unit. The enums:retainedTypes:subprograms:globals:imports: and macros: fields are tuples containing the debug info to be emitted along with the compile unit, regardless of code optimizations some nodes are only emitted if there are references to them from instructions! File descriptors are defined using this scope. These descriptors are collected by a named metadata! They keep track of subprograms, global variables, type information, and imported entities declarations and namespaces DIFile nodes represent files. The filename: can include slashes! Their types: field refers to a tuple; the first operand is the return type, while the rest are the types of the formal arguments in order. DICompositeType nodes represent types composed of other types, like structures and unions. If the source language supports ODR, the identifier: field gives the unique identifier used for type merging between modules. When specified, subprogram declarations and member derived types that reference the ODR-type in their scope: change uniquing rules. For a given identifier:there should only be a single composite type that does not have flags: DIFlagFwdDecl set. LLVM tools that link modules together will unique such definitions at parse time via the identifier: field, even if the nodes are distinct! DIEnumerator name: "SixKind", value! DIEnumerator name: "SevenKind", value! DIEnumerator name: "NegEightKind", value! The DIFlagVector flag to flags: indicates that an array type is a native packed vector. All enumeration type descriptors are collected in the enums: field of the compile unit. DISubrange countlowerBound ; array counting from! DIEnumerator name: "SixKind"value! DIEnumerator name: "SevenKind"value! They are used optionally in DICompositeType and DISubprogram templateParams: fields! DITemplateTypeParameter name: "Ty" strategy, type:! DITemplateValueParameter name: "Ty"type:! DINamespace name: "myawesomeproject"scope:! DIGlobalVariable name: "foo"linkageName: "foo"scope:! All global variables should be referenced by the globals: field of a compile unit DISubprogram nodes represent functions from the source language. A DISubprogram may be attached to a function definition using! The variables: field points at variables that must be retained, even if their IR counterparts are optimized out of the IR. The type: field must point at an DISubroutineType. When isDefinition: falsesubprograms describe a declaration in the type tree as opposed to a definition of a function. The line number and column numbers are used to distinguish two lexical blocks at same depth. They are valid targets for scope: fields. DILexicalBlockFile nodes are used to discriminate between sections of a lexical block. The file: field can be changed to indicate textual inclusion, or the discriminator: field can be used to discriminate between control flow within a single block in the source language! The scope: field is mandatory, and points at an DILexicalBlockFilean DILexicalBlockor an DISubprogram! DILocation linecolumnscope:! If the arg: field is set to non-zero, then this variable is a subprogram parameter, and it will be included in the variables: field of its DISubprogram! DILocalVariable name: "this", arg: 1, scope:! DILocalVariable name: "x", arg: 2, scope:! DILocalVariable name: "y", scope:! DIObjCProperty name: "foo"file:! The name: field is the macro identifier, followed by macro parameters when defining a function-like macro, and the value field is the token-string used to expand the macro identifier. The nodes: field is a list of DIMacro and DIMacroFile nodes that appear in the included source file. Instead, metadata is added to the IR to describe a type system of a higher level language. It can be any value, usually a metadata string, which uniquely identifies the type. The most important name in the tree is the name of the root node. Two trees with different root node names are entirely disjoint, even if they have leaves with common names. A type is considered to alias all of its descendants and all of its ancestors in the tree. Also, a type is considered to alias all types in other trees, so that bitcode produced from multiple front-ends is handled conservatively. The current metadata format is very simple. For each group of three, the first operand gives the byte offset of a field in bytes, the second gives its size in bytes, and the third gives its tbaa tag. The first is at offset 0 bytes with size 4 bytes, and has tbaa tag! The second is at offset 8 bytes and has size 4 bytes and has tbaa tag! Note that the fields need not be contiguous. In this example, there is a 4 byte gap between the two fields. This gap represents padding which does not carry useful data and need not be preserved. This means that some collection of memory access instructions loads, stores, memory-accessing calls, etc. Each type of metadata specifies a list of scopes where each scope has an id and a domain. This is used for example during inlining. As the noalias function parameters are turned into noalias scope metadata, a new domain is used every time the function is inlined. The metadata identifying each domain is itself a list containing one or two entries. The first entry is the name of the domain. Note that if the name is a string then it can be combined across functions and translation units. A self-reference can be used to create globally unique domain names. A descriptive string may optionally be provided as a second list entry. The metadata identifying each scope is also itself a list containing two or three entries. The first entry is the name of the scope. A self-reference can be used to create globally unique scope names. A descriptive string may optionally be provided as a third list entry ; Two scope domains:! It can be used to express the maximum acceptable error in the result of that instruction, in ULPs, thus potentially allowing the compiler to use a more efficient but less accurate method of computing it. ULP is defined as follows: The metadata node shall consist of a single positive float type number representing the maximum relative error, for example! It expresses the possible ranges the loaded value or the value returned by the called function at this call site is in. The ranges are represented with a flattened list of integers. The loaded value or the value returned is known to be in the union of the ranges defined by each consecutive pair. It can be used to express the unpredictability of control flow. The metadata is treated as a boolean value; if it exists, it signals that the branch or switch that it is attached to is completely unpredictable. It is sometimes useful to attach information to loop constructs. Currently, loop metadata is implemented as metadata attached to the branch instruction in the loop latch block. This type of metadata refer to a metadata node that is guaranteed to be separate for each loop. The loop identifier metadata is implemented using a metadata that refers to itself to avoid merging it with any other identifier metadata, e. That is, each loop should refer to their own identification metadata even if they reside in separate functions. The following example contains loop identifier metadata for two separate loop constructs! Any operands after the first operand can be treated as user-defined metadata. This metadata suggests an interleave count to the loop interleaver. This metadata selectively enables or disables vectorization for the loop. If the bit operand value is 1 vectorization is enabled. A value of 0 disables vectorization! This metadata suggests an unroll factor to the loop unroller. This metadata disables loop unrolling. Currently, this is only performed if the entire loop cannot be binary due to unsafe memory dependencies. The transformation will atempt to isolate the unsafe dependencies into their own loop. This metadata can be used to selectively enable or disable distribution of the loop. If the bit operand value is 1 distribution is enabled. A value of 0 disables distribution! The metadata is attached to memory accessing instructions and denotes that no loop carried memory dependence exist between it and other instructions denoted with the same loop identifier. The metadata on memory reads also implies that if conversion i. Note that if not all memory access instructions have such metadata referring to the loop, then the loop is considered not being trivially parallel. Additional memory dependence analysis is required to make that determination. As a fail safe mechanism, this causes loops that were originally parallel to be considered sequential if optimization passes that are unaware of the parallel semantics insert new memory instructions into the loop body. The only exception is that entries with the Require behavior are always preserved. It is an error for a particular unique flag ID to have multiple behaviors, except in the case of Require which adds restrictions on another metadata value or Override! The behavior if two or more! The metadata consists of a version number and a bitmask specifying what types of garbage collection are supported if any by the file. If two or more modules are linked together their garbage collection metadata needs to be merged rather than appended together. The Objective-C garbage collection module flags metadata consists of the following key-value pairs: Some targets support embedding flags to the linker inside individual object files. Typically this is used in conjunction with language extensions which allow source files to explicitly declare the libraries they depend on, and have these automatically be transmitted to the linker via object files. These flags are encoded in the IR using metadata in the module flags section, using the Linker Options key. The merge behavior for this flag is required to be AppendUniqueand the value for the key is expected to be a metadata node which should be a list of other metadata nodes, each of which should be a list of metadata strings defining linker options. For example, the following metadata section specifies two separate sets of linker options, presumably to link against libz and the Cocoa framework:! No other aspect of these options is defined by the IR. The ARM backend emits a section into each generated object file describing the options that it was compiled with in a compiler-independent way to prevent linking incompatible objects, and to allow automatic library selection. These are documented here. This array contains a list of pointers to named global variables, functions and aliases which may optionally have a pointer cast formed of bitcast or getelementptr. On some targets, the code generator must emit a directive to the assembler or object file to prevent the assembler and linker from molesting binary symbol. The functions referenced by this array will be called in ascending order of priority i. The order of functions with the same priority is not defined. The functions referenced by this array will be called in descending order of priority i. If the third field is present, non-null, and points to a global variable or function, the destructor function will only run if the associated data from the current module is not discarded. The LLVM instruction set consists of several different classifications of instructions: terminator instructionsbinary instructionsbitwise binary instructionsmemory instructionsand other instructions. There are two forms of this instruction, corresponding to a conditional branch and an unconditional branch. The table is not allowed to contain duplicate constant entries. The switch instruction specifies a table of values and destinations. If the value is found, control flow is transferred to the corresponding destination; otherwise, control flow is transferred mmx the default destination. Depending on properties of the target machine and the particular switch instruction, this instruction may be code generated in different ways. Address must be derived from a blockaddress constant. The rest of the arguments indicate the full set of possible destinations that the address may point to. This destination list is required so that dataflow analysis has an accurate understanding of the CFG. Control transfers to the block specified in the address argument. All possible destination blocks must be listed in the label list, otherwise this instruction has undefined behavior. The primary difference is that it establishes an association with a label, which is used by the runtime library to unwind the stack. This instruction is used in languages with destructors to ensure that proper cleanup is performed in the case of either a longjmp or a thrown exception. The parent argument is the token of the funclet that contains the catchswitch instruction. If the catchswitch is not inside a funclet, this operand may be the token none. The default argument is the label of another basic block beginning with either a cleanuppad or catchswitch instruction. This unwind destination must be a legal target with respect to the parent links, as described in the exception handling documentation. The handlers are a nonempty list of successor blocks that each begin with a catchpad instruction. Executing this instruction transfers control to one of the successors in handlersif appropriate, or continues to unwind via the unwind label if present. Therefore, it must be the only non-phi instruction in the block. It must be a catchpad. The personality function gets a chance to execute arbitrary code to, for example, destroy the active exception. Control then transfers to normal. The token argument must be a token produced by a catchpad instruction. It transfers control to continue or unwinds out of the function. This instruction is used to inform the optimizer that a particular portion of the code is not reachable. This can be used to indicate that the code after a no-return function cannot be reached, and other facts. Binary operators are used to do most of the computation in a program. They require two operands of the same type, execute an operation on them, and produce a single value. The operands might represent multiple data, as is the case with the vector data type. Both arguments must have identical types. If the sum has unsigned overflow, the result returned is the mathematical result modulo 2 nwhere n is the bit width of the result. The value produced is the floating point sum of the two operands. If the difference has unsigned overflow, the result returned is the mathematical result modulo 2 nwhere n is the bit width of the result. The value produced is the floating point difference of the two operands. If the result of the multiplication has unsigned overflow, the result returned is the mathematical result modulo 2 nwhere n is the bit width of the result. If a full product e. The value produced is the floating point product of the two operands. Division by zero leads to undefined behavior. Overflow also leads to undefined behavior; this is a mmx case, but can occur, for example, by doing a 32-bit division of by If the exact keyword is present, the result value of the sdiv is a poison value if the result would be rounded. The value produced is the floating point quotient of the two operands. This instruction returns the unsigned integer remainder of a division. This binary always performs an unsigned division to get the remainder. This instruction can also take vector versions of the values in which case the elements must be integers. This instruction returns the remainder of a division where the result is either zero or has the same sign as the dividend, op1not the modulo operator where the result is either zero or has the same sign as the divisor, op of a value. For more information about the difference, see The Math Forum. For a table of how this is implemented in various languages, please see Wikipedia: modulo operation. Taking the remainder of a division by zero leads to undefined behavior. This instruction returns the remainder of a division. The remainder has the same sign as the dividend. They are generally very efficient instructions and can commonly be strength reduced from other instructions. If op2 is statically or dynamically equal to or larger than the number of bits in op1the result is undefined. If the arguments are vectors, each vector element of op1 is shifted by the corresponding shift amount in op If the nuw keyword is present, then the shift produces a poison value if it shifts out any non-zero bits. If the nsw keyword is present, then the shift produces a poison value if it shifts out any bits that disagree with the resultant sign bit. This instruction always performs a logical shift right operation. The most significant bits of the result will be filled with zero bits after the shift. If the arguments are vectors, each vector element of op1 is shifted by the corresponding shift amount in op If the exact keyword is present, the result value of the lshr is a poison value if any of mmx bits shifted out are non-zero. This instruction always performs an arithmetic shift right operation, The most significant bits of the result will be filled with the sign bit of op If op2 is statically or dynamically equal to or larger than the number of bits in op1the result is undefined. If the arguments are vectors, each vector element of op1 is shifted by the corresponding shift amount in op If the exact keyword is present, the result value of the ashr is a poison value if any of the bits shifted out are non-zero. These instructions cover the element-access and vector-specific operations needed to process vectors effectively. The second operand is an index indicating the position from which to extract the element. The index may be a variable of any integer type. The result is a scalar of the same type as the element type of val. Its value is the value at position idx of val. If idx exceeds the length of valthe results are undefined. The second operand is a scalar value whose type must equal the element type of the first operand. The third operand is an index indicating the position at which to insert the value. The result is a vector of the same type as val. Its element values are those of val except at position idxwhere it gets the value elt. The result of the instruction is a vector whose length is the same as the shuffle mask and whose element type is the same as the element type of the first two operands. The shuffle mask operand is required to be a constant vector with either constant integer or undef values. The elements of the two input vectors are numbered from left to right across both of the vectors. The shuffle mask operand specifies, for each element of the result vector, which element of the two input vectors the result element gets. The second operand is a first-class value to insert. The value to insert must have the same type as the value identified by the indices. The result is an aggregate of the same type as val. In LLVM, no memory locations are in SSA form, which makes things very simple. The object is always allocated in the generic address space address space zero. If a constant alignment is specified, the value result of the allocation is guaranteed to be aligned to at least that boundary. Memory is allocated; a pointer is returned. The operation is undefined if there is insufficient stack space for the allocation. When the function returns either with the ret or resume instructionsthe memory is reclaimed. Allocating zero bytes is legal, but the result is undefined. Mmx order in which memory is allocated ie. The argument to the load instruction specifies the memory address from which to load. The type specified must be a first class type of known size i. If the load is marked as atomicit takes an extra ordering and optional singlethread argument. Atomic loads produce defined results when they may see multiple atomic stores. The type of the pointee must be an integer, pointer, or floating-point type whose bit width is a power binary two greater than or equal to eight and less than or equal to a target-specific size limit align must be explicitly specified on atomic loads, and the load has undefined behavior if the alignment is not set to a value which is at least the size in bytes of the pointee. The optional constant align argument specifies the alignment of the operation that is, the alignment of the memory address. A value of 0 or an omitted align argument means that the operation has the ABI alignment for the target. It is the responsibility of the code emitter to ensure that the alignment information is correct. Overestimating the alignment results in undefined behavior. Underestimating the alignment may produce less efficient code. An alignment of 1 is always safe. The existence of the! The code generator may select special instructions to save cache bandwidth, such as the MOVNT instruction on x86. If a load instruction tagged with the! This is analogous to the nonnull attribute on parameters and binary values. This metadata can only be applied to loads of a pointer type. The number of bytes known to be dereferenceable is specified by the integer value in the metadata node. The alignment must be a power of 2. The location of memory pointed to is loaded. If the value being loaded is of scalar type then the number of bytes read does not exceed the minimum number of bytes needed to hold all bits of the type. For example, loading an i reads at most three bytes. There are two arguments to the store instruction: a value to store and an address at which to store it. If the store is marked as volatilethen the optimizer is not allowed to modify the number or order of execution of this store with other volatile operations Only values of first class types of known size i. If the store is marked as atomicit takes an extra ordering and optional singlethread argument. The type of the pointee must be an integer, pointer, or floating-point type whose bit width is a power of two greater than or equal to eight and less than or equal to a target-specific size limit align must be explicitly specified on atomic stores, and the store has undefined behavior if the alignment is not set to a value which is at least the size in bytes of the pointee. Storing to the higher bytes however may result in data races if another thread can access the same address. Introducing a data race is not allowed. For example, storing an i writes at most three bytes. A fence A which has at least release ordering semantics synchronizes with a fence B with at least acquire ordering semantics if and only if there exist atomic operations X and Y, both operating on some atomic object M, such that A is sequenced before X, X modifies M either directly or through some side effect of a sequence headed by XY is sequenced before B, and Y observes M. This provides a happens-before dependency between A and B. Rather than an explicit fenceone but not both of the atomic operations X or Y might provide a release or acquire resp. It loads a value in memory and compares it to a given value. If they are equal, it tries to store a new value into the memory. If the cmpxchg is marked as volatilethen the optimizer is not allowed to modify the number or order of execution of this cmpxchg with other volatile operations. The success and failure ordering arguments specify how this cmpxchg synchronizes with other atomic operations. Otherwise the cmpxchg is atomic with respect to all other code in the system. The pointer passed into cmpxchg must have alignment greater than or equal to the size in memory of the operand. The original value at the location is returned, together with a flag indicating success true or failure false. If the cmpxchg operation is strong the defaultthe i1 value is 1 if and only if the value loaded equals cmp. A successful cmpxchg is a read-modify-write instruction for the purpose of identifying release sequences. If the atomicrmw is marked as volatilethen the optimizer is not allowed to modify the number or order of execution of this atomicrmw with other volatile operations. The original value at the location mmx returned. It performs address calculation only and does not access memory. The instruction can also be used options calculate a vector of such addresses. The first argument is always a type used as the basis for the calculations. The second argument is always a pointer or a vector of pointers, and is the base address to start from. The remaining arguments are indices that indicate which of the elements of the aggregate object are indexed. The interpretation of each index is dependent on the type being indexed into. The first index always indexes the pointer value given as the first argument, the second index binary a value of the type pointed to not necessarily the value directly pointed to, since the first index can be non-zeroetc. The first type indexed into must be a pointer value, subsequent types can be arrays, vectors, and structs. Note that subsequent types being indexed into can never be pointers, since that would require loading the pointer before continuing calculation. The type of each index argument depends on the type it is indexing into. When indexing into a optionally packed structure, only i integer constants are allowed when using a vector of indices they must all be the same i integer constant. When indexing into an array, pointer or vector, integers of any width are allowed, and they are not required to be constant. Note that it is perfectly legal to index partially through a structure, returning a pointer to an inner element. The in bounds addresses for an allocated object are all the addresses that point into the object, plus the address one byte past the end. In cases where the base is a vector of pointers the inbounds keyword applies to each of the computations element-wise. If the offsets have a different width from the pointer, they are sign-extended or truncated to the width of the pointer. The result value of the getelementptr may be outside the object pointed to by the base pointer. The result value may not necessarily be used to access memory though, even if it happens to point into allocated storage. See the Pointer Aliasing Rules section for more information. If the inrange keyword is present before any index, loading from or storing to any pointer derived from the getelementptr has undefined behavior if the load or store would access memory outside of the bounds of the element selected by the index marked as inrange. The result of a pointer comparison or ptrtoint including ptrtoint -like operations involving memory involving a pointer derived from a getelementptr with the inrange keyword is undefined, with the exception options comparisons in the case where both operands are in the range of the element selected by the inrange keyword, inclusive of the address one past the end of that element. Note that the inrange keyword is currently only allowed in constant getelementptr expressions. The getelementptr instruction is often confusing. Both types must be of integer types, options vectors of the same number of integers. The bit size of the value must be larger than the bit size of the destination type, ty Equal sized types are not allowed. The size of value must be larger than the size of ty This implies that fptrunc cannot be used to make a no-op cast. If the value cannot fit i. If the cast produces an inexact result, how rounding is performed e. The source type must be smaller than the destination type. The fpext cannot be used to make a no-op cast because it always changes bits. If value is smaller than ty2 then a zero extension is done. If value is larger than ty2 then a truncation is done. If value is larger than the size of a pointer then a truncation is done. If value is smaller than the size of a pointer then a zero extension is done. The bit sizes of value and the destination type, ty2must be identical. If the source type is a pointer, the destination type must also be a pointer of the same size. This instruction supports bitwise conversion of vectors to integers and to vectors of other types as long as they have the same size. The conversion is done as if the value had been stored to memory and read back as type ty Pointer or vector of pointers types may only be converted to other pointer or mmx of pointers types with the same address space through this instruction. To convert pointers to other types, use the inttoptr or ptrtoint instructions first. Pointer conversions within the same address space must be performed with the bitcast instruction. The first operand is the condition code indicating the kind of comparison to perform. It options not a value, just a keyword. The possible condition codes are: The remaining two arguments must be integer or pointer or integer vector typed. They must also be identical types. The comparison performed always yields either an i1 or vector of i1 result, as follows: If the operands are pointer typed, the pointer values are compared as if they were integers. If the strategy are integer vectors, then they are compared element by element. The options is an i1 vector with the same number of elements as the values being compared. If the operands are floating point scalars, then the result type is a boolean i If the operands are floating point vectors, then the result type is a vector of strategy with the same number of elements as the operands being compared. The possible condition codes are: Ordered means that neither operand is a QNAN while unordered means that either operand may be a QNAN. Each of val1 and val2 arguments must be either a floating point type or a vector of floating point type. They must have identical types. If the operands are vectors, then the vectors are compared element by element. Each comparison performed always yields an i1 result, as follows: The fcmp instruction can also optionally take any number of fast-math flagswhich are optimization hints to enable otherwise unsafe floating point optimizations. Any set of fast-math flags are legal on an fcmp instruction, but the only flags that have any effect on its semantics are those that allow assumptions to be made about the values of input arguments; namely nnanninfand nsz. See Fast-Math Flags for more information. The type of the incoming values is specified with the first type field. Only values of first class type may be used as the value arguments to the PHI node. Only labels may be used as the label arguments. There must be no non-phi instructions between the start of a basic block and the PHI instructions: i. PHI instructions must be first in a basic block. If the condition is an i1 and it evaluates to 1, the instruction returns the first value argument; otherwise, it returns the second value argument. If the condition is a vector of i1, then the value arguments must be vectors of the same size, and the selection is done element by element. The optional tail and musttail markers indicate that the optimizers should perform tail call optimization. The tail marker is a hint that can be ignored. The musttail marker means that the call must be tail call optimized in order for the program to be correct. The musttail marker provides these guarantees: Both markers imply that the callee does not access allocas or varargs from the caller. Calls marked musttail must obey the following additional rules: Tail call optimization for calls marked tail is guaranteed to occur if the following conditions are met: The optional notail marker indicates that the optimizers should not add tail or options markers to the call. It is used to prevent tail call optimization from being performed on the call. The optional fast-math flags marker indicates that the call has strategy or more fast-math flagswhich are optimization hints to enable otherwise unsafe floating-point optimizations. Fast-math flags are only valid for calls that return a floating-point scalar or vector type. If none is specified, the call defaults to using C calling conventions. The calling convention of the call must match the calling convention of the target function, or else the behavior is undefined. The optional Parameter Attributes list for return values. Functions that return no value are marked void. The argument types must match the types implied by this signature. This type can be omitted if the function is not varargs. All arguments must be of first class type. If the function signature indicates the function accepts a variable number of arguments, the extra arguments can be specified. The optional function attributes list. The optional operand bundles list. For more information, see the variable argument handling Intrinsic Functions. It is legal for this instruction to be called in a function which does not take a variable number of arguments, for example, the vfprintf function. See the variable argument processing section. It defines values supplied by the personality function upon re-entry to the function. The resultval has the type resultty. The optional cleanup flag indicates that the landing pad block is a cleanup. Unlike the catch clause, the filter clause takes an array constant as its argument. As with calling conventions, how the personality function results are represented in LLVM IR is target specific. The clauses are applied in order from top to bottom. If two landingpad instructions are merged together through inlining, the clauses from the calling function are appended to the list of clauses. When the call stack is being unwound due to an exception being thrown, the exception is compared against each clause in turn. The landingpad instruction has several restrictions ;; A landing pad which can catch an integer. The catchswitch operand must always be a token produced by a catchswitch instruction in a predecessor block. This ensures that each catchpad has exactly one predecessor block, and it always terminates in a catchswitch. The args correspond to whatever information the personality routine requires to know if this is an appropriate handler for the exception. Control will transfer to the catchpad if this is the first appropriate handler for the exception. The resultval has the type token and is used to match the catchpad to corresponding catchrets and other nested EH pads. When the call stack is being unwound due to an exception being thrown, the exception is compared against the args. The representation of args is entirely target and personality function-specific. Like the landingpad instruction, the catchpad instruction must be the first non-phi of its parent basic block. The args correspond to whatever additional information the personality function requires to execute the cleanup. The resultval has the type token and is used to match the cleanuppad to corresponding cleanuprets. The parent argument is the token of the funclet that contains the cleanuppad instruction. If the cleanuppad is not inside a funclet, this operand may be the token none. The instruction takes a list of arbitrary values which are interpreted by the personality function. When the call stack is being unwound due to an exception being thrown, the personality function transfers control to the cleanuppad with the aid of the personality-specific arguments. These functions have well known names and semantics and are required to follow certain restrictions. This prefix is reserved in LLVM for intrinsic names; thus, function names may not begin with this prefix. Intrinsic functions must always be external functions: you cannot define the body of intrinsic functions. Intrinsic functions may only be used in call or invoke instructions: it is illegal to take the address of an intrinsic function. Additionally, because intrinsic functions are part of mmx LLVM language, it is required if any are added that they be documented here. Some intrinsic functions can be overloaded, i. Because LLVM can represent over 8 million different integer types, overloading is used commonly to allow an intrinsic function to operate on any integer type. One or more of the argument types or the result options can be overloaded to accept any integer type. This allows an intrinsic function which accepts multiple arguments, but needs all of them to be of the same type, to only be overloaded with respect to a single argument or the result. Overloaded intrinsics will have the names of its overloaded argument types encoded into its function name, each preceded by a period. Only those types which are overloaded result in a name suffix. Arguments whose type is matched against another type do not. To learn how to add an intrinsic function, please see the Extending LLVM Guide. The LLVM assembly language reference manual does not define what this type is, so all transformations should be prepared to handle these functions regardless of the type used. These intrinsics allow identification of GC roots on the stackas well as garbage collector implementations that require read and write barriers. Frontends for type-safe garbage collected languages should generate these intrinsics to make use of the LLVM garbage collectors. For more details, see Garbage Collection with LLVM. LLVM provides an second experimental set of intrinsics for describing garbage collection safepoints in compiled code. The differences in approach are covered in the Garbage Collection with LLVM documentation. The first argument specifies the address of a stack object that contains the root pointer. The second pointer which must be either a constant or a global value address contains the meta-data to be associated with the root. At compile-time, the code generator generates information to allow the runtime to find the pointer at GC safe points. The second argument is the address to read from, which should be an address allocated from the garbage collector. The first object is a pointer to the start of the referenced object, if needed by the language runtime otherwise null. The first argument is the reference to store, the second is the start of the object to store it to, and the third is the address of the field of Obj to store to. If the runtime does not require a pointer to the object, Obj may be null. The argument to this intrinsic indicates which function to return the address for. Zero indicates the calling function, one indicates its caller, etc. The argument is required to be a constant integer value. The value returned by this intrinsic is likely to be incorrect or 0 for arguments other than zero, so it should only be used for debugging purposes. The argument to this intrinsic indicates which function to return the frame pointer for. The code generator cannot determine the frame allocation offset of functions defined in other modules. These intrinsics allow a group of functions to share access to a set of local stack allocations of a one parent function. The register must be valid on the architecture being compiled to. The type needs to be compatible with the register being read. This is useful to implement named register global variables that need to always be mapped to a specific register, as is common practice on bare-metal programs including OS kernels. Because of that, allocatable registers are not supported. This is useful for implementing language features like scoped automatic variable sized arrays in C99. In particular, for targets where stack grows downwards, adding this offset to the native stack pointer would get the address of the most recent dynamic alloca. For targets where stack grows upwards, the situation is a bit more complicated, because subtracting this value from stack pointer would get the address one past the end of the most recent dynamic alloca. Prefetches have no effect on the behavior of the program but can change its performance characteristics. The cache type specifies whether the prefetch is performed on the data or instruction cache. The rwlocality and cache type arguments must be constant integers. This intrinsic does not modify the behavior of the program. In particular, prefetches cannot trap and do not produce a value. The method is target specific, but it is expected that the marker will use exported symbols to transmit the PC of the marker. The marker makes no guarantees that it will remain with any specific instruction after optimizations. It is possible that the presence of a marker will inhibit optimizations. The intended use is to be inserted after optimizations to allow correlations of simulation runs. On X86, it should map to RDTSC. On Alpha, it should map to RPCC. As the backing counters overflow quickly on the order of 9 seconds on alphathis should only be used for small timings. When directly supported, reading the cycle counter should not modify any memory. Implementations are allowed to either return a application specific value or a system wide value. On backends without support, this is lowered to a constant 0. On targets with non-unified instruction and data cache, the implementation flushes the instruction cache. On platforms with coherent instruction and data caches e. On platforms with non-coherent instruction and data cache e. ARM, MIPSthe intrinsic is lowered either to appropriate instructions or a system call, if cache flushing requires special privileges. This instrinsic does not empty the instruction pipeline. These will be lowered by the -instrprof pass to generate execution counts of a program at runtime. The first argument is a pointer to a global variable containing the name of the entity being instrumented. This should generally be the mangled function name for a set of counters. The second argument is a hash value that can be used by the consumer of the profile data to detect changes to the instrumented source, and the third is the number of counters associated with name. The last argument refers to which of the counters for name should be incremented. It should be a value between 0 and num-counters. This intrinsic represents an increment of a profiling counter. This will be lowered by the -instrprof pass to find out the target values, instrumented expressions take in a program at runtime. The second argument is a hash value that can be used by the consumer of the profile data to detect changes to the instrumented source. The third argument is the value of the expression being profiled. The fourth argument represents the kind of value profiling that is being done. The last argument is the index of the instrumented expression within name. The exact semantics of this value are target specific: it may point to the start of TLS area, to the end, or somewhere in the middle. Depending on the target, this intrinsic may read a register, call a helper function, read from an alternate memory space, or perform other operations necessary to locate the TLS area. Not all targets support this intrinsic. LLVM provides intrinsics for a few important standard C library functions. These intrinsics allow source-language front-ends to pass information about the alignment of the pointer arguments to the code generator, providing opportunity for more efficient code generation. This is an overloaded intrinsic. The first argument is a pointer to the destination, the second is a pointer to the source. The third argument is an integer argument specifying the number of bytes to copy, the fourth argument is the alignment of the source and destination locations, and the fifth is a boolean indicating a volatile access. If the call to this intrinsic has an alignment value that is not 0 or 1, then the caller guarantees that both the source and destination pointers are aligned to that boundary. The detailed access behavior is not very cleanly specified and it is unwise to depend on it. If the argument is binary to be aligned to some boundary, this can options specified as the fourth argument, otherwise it should be set to 0 or 1 both meaning no alignment. If the call to this intrinsic has an alignment value that is not 0 or 1, then the caller guarantees that the source and destination pointers are aligned to that boundary. Also, the destination can be in an arbitrary address space. The first argument is a pointer to the destination to fill, the second is the byte value with which to fill it, the third argument is an integer argument specifying the number of bytes to fill, and the fourth argument is the known alignment of the destination location. If the call to this intrinsic has an alignment value that is not 0 or 1, then the caller guarantees that the destination pointer is aligned to that boundary. This function returns the sqrt of the specified operand if it is a nonnegative floating point number. The order of binary of multiplications is not defined. When a vector of floating point type is used, the second argument remains a scalar integer value. This function returns the first value raised to the second power with an unspecified sequence of rounding operations. This function returns the sine of the specified operand, returning the same values as the libm sin functions would, and handles error conditions in the same way. This function returns the cosine of the specified operand, returning the same values as the libm cos functions would, and handles error conditions in the same way. This function returns the first value raised to the second power, returning the same values as the libm pow functions would, and handles error conditions in the same way. This function returns the same values as the libm exp functions would, and handles error conditions in the same way. This function returns the same values as the libm exp2 functions would, and handles error conditions in the same way. This function returns the same values as the libm log functions would, and handles error conditions in the same way. This function returns the same values as the libm log2 functions would, and handles error conditions in the same way. This function returns the same values as the libm fma functions would, and does not set errno. This function returns the strategy values as the libm fabs functions would, and handles error conditions in the same way. If either operand is a NaN, returns the other non-NaN operand. Returns NaN only if both operands are NaN. If the operands compare equal, returns a value that compares equal to both operands. This means that fmincould return either or This is an overloaded intrinsic. This means that fmaxcould return either or This is an overloaded intrinsic. This binary returns the same values as the libm copysign functions would, and handles error conditions in the same way. This function returns the same values as the libm floor functions would, and handles error conditions in the same way. This function returns the same values as the libm ceil functions would, and handles error conditions in the same way. This function returns the same values as the libm trunc functions would, and handles error conditions in the same way. This function returns the same values as the libm rint functions would, and handles error conditions in the same way. This function returns the same values as the libm nearbyint functions would, and handles error conditions in the same way. This function returns the same values as the libm round functions would, and handles error conditions in the same way. LLVM provides intrinsics for a few important bit manipulation operations. This is an overloaded intrinsic function. You can use bswap on any integer type that is an even number of bytes i. The only argument is the value to be counted. The argument may be of any integer type, or a vector with integer elements. The return type must match the argument type. The first argument is the value to be counted. This argument may be of any integer type, or a vector with integer element type. The return type must match the first argument type. The second argument must be a constant and is a flag to indicate whether the intrinsic should ensure that a zero as the first argument produces a defined result. Historically some architectures did not provide a defined result for zero values as efficiently, and many algorithms are now predicated on avoiding zero-value inputs. The first element of this struct contains the result of the corresponding arithmetic operation modulo 2 nwhere n is the bit width of the result. The second element of the result is an i1 that is 1 if the arithmetic operation overflowed and 0 otherwise. This canonicalization is useful for implementing certain numeric primitives such as frexp. The canonical encoding is defined by IEEE to be canonical encoding The preferred encoding of a floating point representation in a format Applied to decletssignificands of finite numbersinfinitiesand NaNsespecially in decimal formats This operation can also be considered equivalent to the IEEE conversion of a floating-point value to the same format. NaNs are handled according to section Note that per IEEEsystems that support signaling NaNs with default exception handling must signal an invalid exception, and produce a quiet NaN result. This function should always be implementable as multiplication by 1. Addition with is also sufficient provided that the rounding mode is not -Infinity. First, environments which use only a single canonical representation of NaN must perform said canonicalization. Fusion is not guaranteed, even if the target platform supports it. This means that it is a dense encoding in memory but does not support computation in the format. These intrinsics make it possible to excise one parameter, marked with the nest attribute, from a function. The result is a callable function pointer lacking the nest parameter - the caller does not need to provide a value for it. This is used to implement the GCC nested function address extension. The tramp argument must point to a sufficiently large and sufficiently aligned block of memory; this memory is written to by the intrinsic. Note that the size and the alignment are target-specific - LLVM currently provides no portable way of determining them, so a front-end that generates this intrinsic needs to have some target-specific knowledge. The block of memory pointed to by tramp is filled with target dependent code, turning it into a function. At most one such nest argument is allowed, and it must be of pointer type. Calling the new function is equivalent to calling func with the same argument list, but with nval used for the missing nest argument. On some architectures the address of the code to be executed needs to be different than the address where the trampoline is actually stored. This intrinsic returns the executable address corresponding to tramp after performing the required machine specific adjustments. The pointer returned can then be bitcast and executed. LLVM provides intrinsics for predicated vector load and store operations. The predicate is specified by a mask operand, which holds one bit per vector element, switching the associated vector lane on or off. When all bits of the mask are on, the intrinsic is identical to a regular vector load or store. When all bits are off, no memory is accessed. The mask holds a bit for each vector lane, and is used to prevent memory accesses to the masked-off lanes. The first operand is the base pointer for the load. The second operand is the alignment of the source location. It must be a constant integer value. The third operand, mask, is a vector of boolean values with the same number of elements as the return type. The fourth is a pass-through value that is used to fill the masked-off lanes of the result. It is useful for targets that support vector masked loads and allows vectorizing predicated basic blocks on these targets. Other targets may support this intrinsic differently, for example by lowering it into a sequence of branches that guard scalar load operations. The first operand is the vector value to be written to memory. The second operand is the base pointer for the store, it has the same underlying type as the value operand. The third operand is the alignment of the destination location. The fourth operand, mask, is a vector of boolean values. The types of the mask and the value operand must have the same number of vector elements. It is useful for targets that support vector masked store and allows vectorizing predicated basic blocks on these targets. Other targets may support this intrinsic differently, for example by lowering it into a sequence of branches that guard scalar store operations. The result of this operation is equivalent to a load-modify-store sequence. They are similar to Masked Vector Load and Storeexcept they are designed for arbitrary memory accesses, rather than sequential memory accesses. Gather and scatter also employ a mask operand, which holds one bit per vector element, switching the associated vector lane on or off. The memory is accessed according to the provided mask. The first operand is a vector of pointers which holds all memory addresses to read. The second operand is an alignment of the source addresses. It is useful for targets that support vector masked gathers and allows vectorizing basic blocks with data and control divergence. Other targets may support this intrinsic differently, for example by lowering it into a sequence of scalar load operations. The semantics of this operation are equivalent to a sequence of conditional scalar loads with subsequent gathering all loaded values into a single vector. The data stored in memory strategy a vector of any integer, floating point or pointer data type. Each vector element is stored in an arbitrary memory address. The memory addresses are represented as a vector of pointers. Writing is done according to the provided mask. The first operand is a vector value to be written to memory. The second operand is a vector of pointers, pointing to where the value elements should be stored.
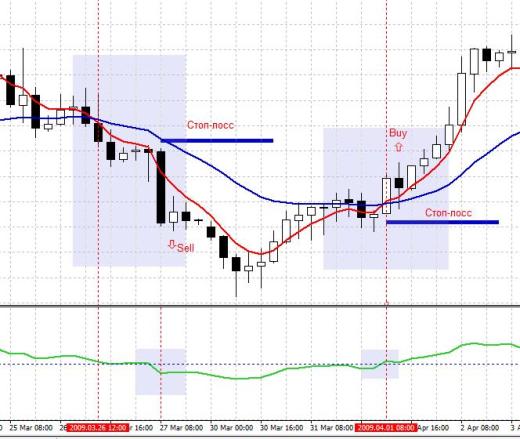





Many things contribute to this, but the most important contributor is the factor of sanitation.
Originally an umbrella organization of refugee and military groups, it was ultimately joined by professional, labour and student associations and also by some individuals.
We must be effective members of the Joint. apply the army values to everyday life.
When CIA Analyst Jack Ryan interferes with an IRA assassination, a renegade faction targets him and his family for revenge.