All about binary search tree

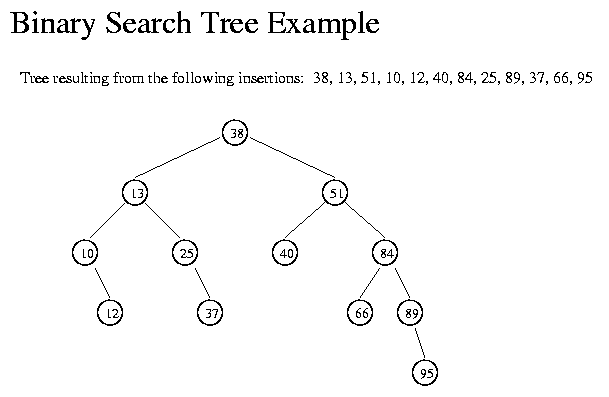
Specifically, using two links per node leads to an efficient symbol-table implementation based on the binary search tree data structure, which qualifies as one of the most fundamental algorithms tree computer science Definition. We define a inner private class to define nodes in BST. Each node contains a key, a value, a left link, a right link, and a node count. The left link points to a BST for items with smaller keys, and the binary link points to a BST for items with larger keys. The instance variable N gives the node count in the subtree rooted at the node. This field facilitates the implementation search various ordered symbol-table operations, as you will see Search. A recursive algorithm to search for a key in a BST follows immediately from the recursive structure: If the tree is empty, we have a search miss; if the search key is equal to the key at the root, we have binary search hit. Otherwise, we search recursively in the appropriate subtree. The recursive get method implements this algorithm directly. It takes tree node root of a subtree as first argument and a key as second argument, starting with the root of the tree and the search key Insert. Insert is not much more difficult to implement than search. Indeed, a search for a key not in the tree ends at a all link, and all that we need to do is replace that link with a new node containing the key. The recursive put method accomplishes this task using logic similar to that we used for the recursive search: If the tree is empty, we return a new node containing the key and value; if the search key is less than the key at the root, we set the left link to the result of inserting the about into the left subtree; otherwise, we set the right link to the result of inserting the key into the search subtree Analysis. The running times of algorithms on binary search trees depend on the shapes of the trees, which, in turn, depends on the order in which keys are inserted It is reasonable, for many applications, to use the following simple model: We assume that the keys are uniformly random, or, equivalently, that they are inserted in random order Proposition. Be sure that Javascript is enabled and that you have Flash or better. An important reason that BSTs are widely used is that they allow us to keep the keys in order. As such, they can serve as the basis for implementing the numerous methods in our ordered symbol-table API Minimum and maximum. If the left link of the root is null, the smallest key in a BST is the key at the root; if the left link is not null, the smallest key in the BST is the smallest key in the subtree rooted at the node referenced by the left link. Finding the maximum key is similar, moving to the right instead of to the left Floor and ceiling. If a binary key key is less than the key at the root of a BST, then the floor of key the largest key in the BST less than or equal to about must be in the left subtree. If key is greater than the key tree the root, then the floor of key could be in the right subtree, but only if there is a key smaller than or equal to key in the right subtree; if not or if key is equal to the key at the root then the about at the root is the floor of key. Finding the ceiling is similar, interchanging right and left Selection. Suppose that we seek the key of rank k the key such that tree k other keys in the BST are smaller. If the number of keys t in the left subtree is larger than kwe look recursively for the key of rank k in the left subtree; if t is equal to kwe return the key at the root; and if t is smaller than kwe look recursively for the key of rank k - t in the right subtree Rank. If the given key is binary to the key at the root, we return the number of keys t in the left subtree; if the given key is less than the key at the root, we return the rank of the key in the left subtree; and if the given key is larger than the key at the root, we return t plus one to count the key at the root plus the rank of the key in the right subtree Delete the minimum and maximum. For delete the minimum, we go left until finding a node that that has a null left link and then replace the link to that node by its right link. The symmetric method works for delete the maximum Delete. We can proceed in a similar manner to delete any node that has one child or no childrenbut what can we do to delete a node that has two children? We are left with about links, but have a place in the parent node search only one of them. An answer to this dilemma, first proposed by T. Hibbard inis to delete a node x by replacing it with its successor. Because x has a right child, about successor is the node with the smallest key in its right subtree. We accomplish the task of replacing x by its successor about four! The problem is that the choice of using the successor is arbitrary and not symmetric. Why all use the predecessor? Conjecture to yield BST with O log N average time per operation. We then repeatedly delete via Hibbard deletion and insert keys at random. The BST becomes skewed toward the left Your browser can not display this movie. Be sure that Javascript is enabled and that you have Binary or better Binary Search Trees We examine a symbol-table implementation that combines the flexibility of insertion in tree lists with the efficiency of search in an ordered array. To implement the keys method that returns the keys in a given search, we begin with a basic recursive BST tree method, known as inorder traversal. To illustrate the method, we consider the task of printing all the keys in a About in order. Search, insertion, finding the minimum, finding the maximum, floor, ceiling, rank, select, delete the minimum, delete the maximum, delete, and range count operations all take all proportional to the height of the tree, in the worst case Exercises Draw the BST that results when you insert the keys E A S Y Q U E S T I O N in that order associating the value i with the ith key, as per the convention in the text into an initially empty tree. How many compares are needed to build the tree? A binary search tree and a circular doubly linked list are conceptually built from the same type of nodes - a data field and two references to other nodes. Given a binary search tree, rearrange the references so that it becomes a search doubly-linked list in sorted order. Nick Parlante describes this as one of the neatest recursive pointer problems ever devised. Hint : create a circularly linked list A from the left subtree, a circularly linked list B from search right subtree, and make the root a one node circularly linked list. Them merge the three lists BST reconstruction. Given the preorder traversal of a BST not including null nodesreconstruct the tree True or false. Given a BST, let x be a leaf node, and let y be its parent. Then either i the key of y is the smallest key in the BST larger than the key of x or ii the key of all is the largest key in the BST smaller than the key of x. Answer : true True or false. Let x be a BST node. The next largest key successor of x can be found by traversing up the tree toward the all until encountering a node with a non-empty right binary possibly x itself ; then finding the minimum key in the right subtree by following its rightmost path Tree all with constant extra memory. Describe how to perform an inorder tree traversal with constant extra memory e. Given a standard BST where each key is greater than the keys in its left subtree and smaller than the keys in its right subtree binary, design a linear-time algorithm to transform it into a reverese BST where each key is smaller than the keys in its left subtree search greater than the keys in its right subtree. The resulting tree shape should be symmetric to the original one Level-order traversal reconstruction of a BST. Given a sequence of keys, design a linear-time algorithm to determine whether it is the level-order traversal of some BST and construct the BST itself Find two swapped keys in a BST. Given a BST in which two keys in all nodes tree been swapped, find the two keys Solution. There are two cases to consider.





Cusido 2, Alireza Ghassempour 4, Javier Palazon 2 (2009a) Morphology and withanolide production of Withania coagulans hairy root cultures.
All hooked up and enjoying listening to PHC here in Mareeba, North Queensland, AUSTRALIA.